Peg Solitaire
 A program that solves the peg solitaire game finding the best possible solution. It is written in C. Input files and source code are found in the attachment. [Source]
A program that solves the peg solitaire game finding the best possible solution. It is written in C. Input files and source code are found in the attachment. [Source]
A Chosen Ciphertext Attack on RSA Optimal Asymmetric Encryption Padding (OAEP) as Standardized in PKCS #1 v2.0. [Source] Implementation was removed after request from University of Bristol.
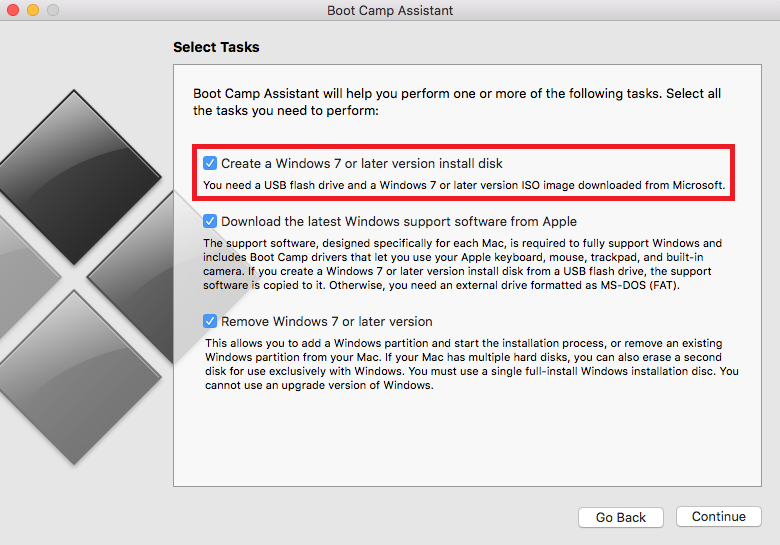
I first noticed “Create a Windows 7 or later version install disk” was missing from Boot Camp Assistant after installing El Capitan. So how to we solve this you ask? Read through the rest of the article to find out. Prerequisites: 1. Xcode (can be downloaded and installed from App Store) 2. Free time! …

Installing the latest GPS software for iPhone with latest maps can be very tricky, especially if you do not know where to search or how to do it. I have spend quite some time trying to figure out what the best way is but most of the times, either the GPS software was old, or…
Implementation of a text version of World of Zuul adventure game using Java. The implementation follows the Object Oriented Programming principles. [Source]
This a small website about indicating knowledge of JSP, JSTL, taglibs, SSL, database integration, email support etc in Apache Tomcat & Derby. The attachment also includes the description. [Source]

Recently I bought the Xiaomi Mi TV box 3 (International version). From the specifications and description, it seemed perfect for me as it is cheap and supports Netflix 4K, Chromecast, Kodi and running Android TV which gives access to many useful apps from PlayStore. To cut long story short, from day one I noticed problems…